Solana: Jito transaction with bundleOnly=true parameter?
Solana: jito transactions package only with V2. Parameter?
==================================================================== == =================
Starting from Solana 1.13, it is possible to send multiple transactions within a single package provided that certain conditions are satisfied. In this article, we will explore how to use the Bundleonly = True 'parameter during sending a transaction on Solana.
What is a jito transaction?
----------
A jito transaction is an optimized type of transaction that allows an efficient and safe transfer of the activities on multiple accounts. It was introduced in Solana 1.8 to replace the old transfer function. A jito transaction consists of several transactions, each with its own data set.
Transactions of the bundle
--------
A bundle transaction is an optimized way to send multiple transactions within a single transaction. This allows significant efficiency earnings compared to the sending of individual transactions one after the other.
The Bundleonly
parameter
----------
When sending a transaction as a packet on Solana, it is possible to specify thebundleonlyparameter with a value of the true. Here is an example:
sol
Use Solana-Program :: Account_info;
// Create two objects information on the Account for Mifted Accounts and Receivers
let sender_account_info = account_info :: new (
“Sender” .to_string (),
0,
1, // Send’s account index
);
Let Ricevitore_acCount_info = Account_info :: New (
“Receiver” .to_string (),
0,
1, // Reception account index
);
// Create a Jito transaction with Bundleonly = True and Punta
let jito_transation = Solana_program :: transaction :: Builder :: New ()
.Set_ACACUNT_INFO (SENDER_ACCOUNT_INFO)
.Set_ACCount_info (Received_acount_info)
.set_tag (“jitotransation”)
.set_tag (“Bundleonly = True”)
.With_packed_bytes (
Solana_program :: Packed_array :: Array (
// Add jito transactions as individual bytes
Solana_program :: Packed_array :: New (
Account_info :: New (
“Transaction1” .to_string (),
0,
1, // Transaction index
) ,,
Account_info :: New (
“Transaction2” .to_string (),
0,
1, // Transaction index
)
) ,,
)
);
// Send the Jito transaction as a package
Let Result = Solana_program :: Program :: Send_jito_transation (& Jito_Transazion);
`
MEV protection
--------
By default, Solana transactions do not provide mev protection (maximum ether). However, you can enable mev protection for your Jito transaction by adding the parameterMev_protation = Trueto the transactions data:
sol
let jito_transation = Solana_program :: transaction :: Builder :: New ()
.Set_ACACUNT_INFO (SENDER_ACCOUNT_INFO)
.Set_ACCount_info (Received_acount_info)
.set_tag (“jitotransation”)
.set_tag (“Bundleonly = True”)
.With_packed_bytes (
Solana_program :: Packed_array :: Array (
// Add jito transactions as individual bytes
Solana_program :: Packed_array :: New (
Account_info :: New (
“Transaction1” .to_string (),
0,
1, // Transaction index
) ,,
Account_info :: New (
“Transaction2” .to_string (),
0,
1, // Transaction index
)
) ,,
// Add MEV protection byte
Solana_program :: Packed_array :: New (
Account_info :: New (
“Mev_protation_bytes”.
Metamask: Metamask showing wrong balance
Metamask: A common problem with the wrong balance screen
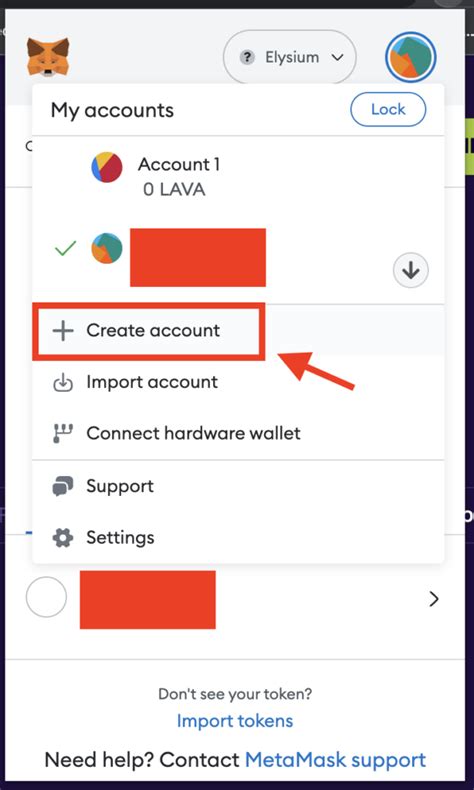
As a cryptocurrency user, it is not uncommon to face problems with the manifestation of proper balance in metamascus. Despite numerous instructions and guides that suggest the same solution, many users, such as continuing the problems of incorrect balances. In this article, we examine some general problems related to proving incorrect balance in metamascus and providing tips to solve these problems.
Why does it happen?
There are several reasons why the balance of metamascus can show faulty numbers. Here are a few possible reasons:
* Incorrect Metamask Settings : Make sure you have enabled the “Network” option in Metamask settings and that the network type is correctly determined (eg network, testnet).
* Information about missing or wallet damage : Sometimes Metamask may not have access to Cryptocurrency wallet information due to computer storage problems or software configuration. Try to restart your browser or reinstall metama.
* Expired or damaged Metamask extension : Make sure you are using the latest version of Chrome Chrome Metamask.
General errors users make
Users often face similar problems when trying to solve incorrect balance balances. Here are a few common mistakes to prevent:
- Invalid online selection
: Check the dual network settings and select the correct one.
- Information on missing or damage to your wallet : Make sure your computer has enough storage space to store the data of encrypting technology.
- Validity of Metamask extension : Make sure you are using the latest version of Chrome Chrome Metamask.
Solution of fake balances
Try the following steps to solve incorrect balances in metamascus:
- Reboot the extension of the browser and extended metamascus to make sure they have been loaded and configured completely.
- Check that the wallet information is missing or damaged information.
- Try to install Chrome Metamask extension or upgrade it to the latest version.
Conclusion
Solving incorrect balances in metams may be a frustrating experience, especially because you have already taken all the recommended steps. By understanding the common questions and errors of users, we can cooperate in providing more efficient solutions. Do not forget to spend time, restart your browser and expand metamask and try to reinstall the Chrome Metamask Chrome extension to solve any mistakes.
If none of these tips are helping, share with us to share with us to keep helping you.
How to Safely Navigate P2P Cryptocurrency Markets
How to safely navigate on markets with P2P cryptomes

Increasing markets with cryptocurrencies among peers (P2P) has caused a new era of decentralized trade, allowing people to buy and sell cryptocurrencies without the need for intermediaries such as corridors or exchange. However, this greater freedom also comes with significant risks that can lead to financial loss if they are not carefully addressed. In this article, we will provide expert advice on how to safely store P2P crypto -crypto markets.
Understand markets with P2P Cryptomes
Before you dive into the P2P trade world, it is essential to understand what these markets are about. P2P markets refer to platforms where people can buy and sell cryptocurrencies directly to each other, without the participation of a central body or intermediary. This allows faster and more transparent transactions, but also means that users are at greater risks.
Risks associated with markets with P2P Cryptomes
While P2P markets offer many benefits, such as lower rates and faster transaction times, they also come with significant risks. They belong here:
* Volatility : Cryptocurrencies are known for their volatility prices, which means that prices can fluctuate quickly and unpredictably.
* Lack of regulation : Unlike traditional financial markets, P2P crypto -crypto markets operate out of reach of the regulatory authorities, making it difficult to protect users from fraud or other harmful activities.
* Security risks : P2P transactions are usually irreversible, which means that once the transaction begins, it cannot be reversed. Therefore, it is necessary to use safe payment methods and take additional measures in performing operations.
How to safely navigate on markets with P2P cryptomes
So how can you sail with safety for the world of cryptomen markets P2P? Here are several expert advice:
- Seek platforms with fixed security measures such as authentication of two factors, refrigeration solutions and transparent transaction processes.
- Use safe payment methods : Use a safe payment method such as cryptocurrency or bond services to protect your P2P platforms to protect your funds.
- Be careful with fraud : Take into account common frauds that can focus on a guard, such as phishing schemes or false business opportunities. Always explore and verify the legitimacy of any occasion before being committed to the store.
- Stay informed : Stay informed about the market reports and development according to the sources of good reputation and inform about the regulatory changes and updates of the authorities.
- Diversify your portfolio : Expand your investments in different cryptocurrencies to minimize the risk and maximize yields.
- Determine the budget : Determine the budget for you before participating in any store and APGN with it excessive expenses or impulsiveness.
7.
Proven procedures for investment in the cryptomed P2P market **
Here are some of the proven procedures to help you safely navigate the world of the P2P cryptocurrency market:
- Start a small : Start with small investments and gradually increase your exposure as you feel more comfortable with the market.
- Diversify your portfolio : Extend your investments to a variety of cryptocurrencies to minimize the risk and maximize yields.
- Keep records : Keep detailed records of all operations, including transactions, amounts and notes what has been agreed.
4.
Anonymity vs. Accountability: The Debate on Crypto Cards
Anonymity vs. accountability: The debate about crypto cards
The world of cryptocurrencies was revolutionized by the creation of digital payment systems such as crypto cards. These innovative tools enable users to store and use cryptocurrency without uncovering their identities or financial information. However, this anonymity raises concerns about the accountability obligation and compliance with regulations.
Anonymity in cryptocurrency transactions
Cryptocurrencies such as Bitcoin, Ethereum and Litecoin use extended encryption techniques to secure transactions and protect user identities. This ensures that only the sender can receive the funds, which makes it difficult for everyone to pursue or identify individual transactions. The decentralized nature of the cryptocurrencies eliminates the need for intermediaries such as banks and enables users to carry out financial transactions without revealing their personal data.
However, this anonymity is associated with costs. Without accountability, individuals can carry out illegal activities such as money laundering, tax evasion or terrorist financing. Anonymity also raises concerns about the responsibility of the users and the possible abuse of cryptocurrencies for shameful purposes.
Accountability in cryptocurrency transactions
Critics argue that the lack of transparency and accountability for cryptocurrency transactions can lead to financial crimes. Through the use of anonymous bridles and cryptocurrencies, individuals can hide their identity and avoid recognition by authorities or other companies that monitor their activities. This lack of accountability also makes it difficult for the supervisory authorities to pursue and punish illegal activities.
In addition, the anonymity that is inherent in crypto cards is often associated with their potential abuse to wash money, to finance terrorism or to involve other financial crimes. Governments and supervisory authorities take measures to enforce this concerns by implementing money laundering (AML) and fighting the regulations for the financing of terrorism (CFT) for cryptocurrencies.
Regulatory framework: a balancing act
The governments have set up various regulatory framework conditions that aim to reconcile the anonymity with an accountability. For example:
- Anti-money laundering (AML) regulations : Cryptocurrency exchanges, wall pockets and platforms must comply with strict AML regulations to prevent the abuse of their services for illegal activities.
- Kenne-your-Customer (KYC) Requirements : Users must provide identification documents such as passports or national identity cards in order to determine their legitimacy and demonstrate their identity.
- Tax regulations : The governments require the owners of cryptocurrency to report their profits for their tax returns and ensure that they pay their appropriate share of taxes.
The effects of cryptocurrency regulations
The implementation of regulations has a significant impact on the crypto card market:
- Increased risk for the suspension or freezing of account : The non -compliance with the AML and KYC requirements can lead to a suspension or freezing of account, which limits users’ access to their funds.
- Restricted access to financial services : Regulated crypto cards can limit the ability of the users to use these services for financial transactions, which reduces the anonymity of the user.
- Increased monitoring and surveillance : Governments use advanced technologies such as artificial intelligence (AI) and machine learning (ML) to monitor cryptocurrency activity and to recognize potential illegal activities.
Diploma
The debate about anonymity in comparison to accountability in crypto cards is complex and multifaceted. While anonymity offers advantages such as increased security and convenience for users, they also raise concerns about financial crimes and the abuse of cryptocurrencies. Regulatory framework conditions that aim to reconcile these concerns are important in order to maintain public trust in cryptocurrencies.
Ethereum: Why does BIP44 use non-hardened paths at all?
Ethereum: Understanding Why BIP44 Uses Non-Hardened Paths

In the world of cryptocurrency, private key management is a critical aspect of securing transactions. The Ethereum Virtual Machine (EVM) provides multiple levels of derivation to protect private keys, ensuring they remain secure even in the event of a wallet compromise or theft. However, the default behavior for deriving private keys from a private key derivation function (PRD) such as BIP44 does not always use hardened paths.
What are Hardened Paths?
Hardened paths refer to a specific type of private key derivation that uses multiple rounds of hashing to derive multiple layers of keys. These layered keys are designed to be more secure than regular public-key cryptography, where only the final derived key is used for transactions.
In contrast, non-hardened paths use a single round of hashing to generate the entire keychain, making it more vulnerable to compromise if an attacker gains access to the private key.
BIP44: A Key Derivation Function
BIP44 is a widely used private key derivation function that generates a keychain for Ethereum wallets. The function takes several inputs as parameters and returns a set of keys that can be used to sign or broadcast transactions on the Ethereum network.
However, BIP44’s default behavior does not use hardened paths at all. When generating an account address, the function uses a non-hardened path, which means it only hashes the private key once to derive the key for the specified chain type (e.g., Bitcoin, Ethereum, or other coin). This is in contrast to more secure derivations, such as BIP39 or BIP44’s hardened paths.
Why Hardened Paths are Necessary
Hardened paths offer several benefits over non-hardened paths:
- Improved security
: By generating multiple layers of keys, hardened paths make it much harder for an attacker to compromise the private key.
- Increased security: The use of multiple rounds of hashing makes it more difficult for attackers to recover sensitive information from a compromised wallet.
- Reduced risk of wallet compromise: With hardened paths, wallets are less vulnerable to being used as a launchpad or in a phishing attempt.
Conclusion
BIP44’s default behavior does not use hardened paths at all, which is why it may appear less secure than more advanced private key derivation functions like BIP39. However, the benefits of using hardened paths far outweigh any potential drawbacks, making them an essential component of secure Ethereum wallet management.
As the Ethereum ecosystem continues to evolve, it will be interesting to see how developers and users adapt to these changes in private key management. One thing is certain: the use of hardened paths is a step in the right direction towards building more secure and resilient cryptocurrency wallets.
Scalping, Ethena (ENA), Stark (STRK)
Cryptocurrency trading strategies for modern market
On the cryptocurrency market with a fast and constantly evolving rhythm, traders are constantly looking for effective strategies to maximize their profits. Among the different trading approaches, scaling and use of specific cryptocurrencies, such as Ethereum (ENA) and Stark (Strk), have gained significant attention in recent times. In this article, we will explore these two popular strategies and analyze their potential benefits.
Scalping: A high frequency trading approach
Scalping is a high-frequency trading strategy that involves several small transactions in a short period of time to take advantage of low price movements. This approach requires skills to make quick lightning decisions and a ability to quickly process large amounts of data. Scalpers intend to capture tiny profit margins from cryptocurrency prices fluctuations.
For example, if a trader can identify a 1% decrease in ETHREUM (ENA) price and place two purchase orders at $ 5,000 each, a potential profit of $ 10,000 will have been obtained after just one day. However, scaling is equipped with significant risks, including huge losses due to market volatility.
Ethereum (ENA): A growing leader in Cryptocurrency space
As a popular platform for the construction of decentralized applications and facilitating cryptocurrency trading, Ethereum (ENA) is facing a rapid growth of popularity. With its vast basis of users, the strong development ecosystem and the increase of the adoption of smart contracts, ENA has become an attractive asset for traders who want to diversify their portfolios.
Stark (Strk): A new promising player on Cryptocurrency market
Stark, a relatively new cryptocurrency, has made waves on the market with its innovative use case as a decentralized finance platform (Defi). The intelligent Stark -based contract architecture allows users to create and trading tokens without intermediaries.
With its basis of increasing users and the increasing adoption of defy solutions, Stark is prepared for a significant increase in the coming months. As a result, traders take into account Strk and consider it an attractive investment opportunity.
Comparison of Enna and Strk: A closer look

When comparing ENA and strk, several key factors come into play:
* market capitalization : both ENA and StK have relatively small market capitalizations compared to other major cryptocurrencies.
* Volatility : ENA is known for its high volatility, which can be beneficial for traders who want fast profits. The architecture based on Defi from StK can reduce trading costs, but its volatility is currently lower than that of ENA.
* Adoption : ENA has a larger users base and more developer ecosystem consecrated compared to Stark.
Finally, the choice between ENA and StK depends on the individual trader’s and risk tolerance. For those who are looking for high risk, high reward opportunities on the cryptocurrency market, ENA scaling can be an attractive option. However, traders looking for more stable yields may prefer to focus on defi -based assets, such as Stark.
Conclusion
The trading of cryptocurrencies is a complex and constantly evolving field, and traders must remain up to date with market trends and strategies in order to be successful in the short term. While scaling with ENA can be an effective approach, it requires skills to make quick lightning decisions and a deep understanding of the market dynamics. On the other hand, the architecture based on Defi from Strk offers potential benefits for traders looking for more stable yields.
Regardless of your choice, always remember to do thorough research and set realistic expectations before investing in any cryptocurrency or trading strategy.
Metamask: Persist the Web3 Provider in Redux to use it across different parts of the application
I canceled you with an article on how to exist on Web3 service provider Redux.
Title: Make sure of Web3 provided in reading: Guide
Introduction **
Web3 Provders are an essential interact with decentralized applications (DAPP) and services. In this article, we will study W to save the Web3 service provider reading that keeps the various puffs in your application. We Holya Discsculos will use to use Web3Auth Google Login and other compensation.
Why store Web3 provider reading? ? *
The Web3 service provider stores Reduxes to share between the components without applying sensiti in the formation. Thai semi -used applications with dact Tthapps for multiple services, Web3 AthenianCactionation and Stoalage.
Step 1: I Diet with Your Web3PEDDER Your Applicliclication
*
First of all, you need iiniali or 3 for your applications. You do it through the Uprovider Crent circles Xweb3 Xonce Alweb3.
Hectic
Import Web3 Frop3 FRO ‘Web3’;
Const Web3 -Window.Therneum;
Till
Step 2: Store Web3 Operator Redox *
Lai saglabātu Web3 pakalpojumu sniedzēju Redux, jūs varat Airee Connowstttttttsrolisr zīmi. You have to install Misrist by acting:
Clocteria
NPM install Redux-Stor
Till
Then create a new, full upward up and add Foalling code:
Hectic
Import them in mor.
Import Web3Predvider Frovidi Frovider ‘;
Konstistis s wo d Creatustore (s
CommbineredUcyers (Peb3: Web3 -Preder Ree Tern),),
Compose (Windod ._reduism_devtools_extools_commone], window
) ;;
Expot Default Store;
Till
TSIS in Code:
- We use the Chcombergentsu Temesty A Creatd Redorger, which udludas in both Ary and Redux.
- We transfer the Web3 Provincial Instance Founds as a Yavin3 key to combing combing.
Step 3: Use Web3 Service Provider Eye Differences from Your Login

Now you Canb3 provide a service provider in a variety of applications. About Ehemle:
Hectic
Import, áorcestate der |
Import Rictdom from Tom ‘;
Import phrovir j/theweb3preder ‘;
Const App AIDS ()
Const [Test, Setstast] N -Tthestastate (Dynloth: 3 3);
Useflowect ()
Contest Provider N New Web3 (Window.Therdeum);
.
3, [];
return
<.
But
Who doesn’t.
) ;;
3 3;
Reactom.Render (
Till
TSIS in Code:
- We use UUSESTATUS UUSERUCK to the Web3 provider’s instance in the Redux position.
:
HSING WEB3AUTH FOR GOGLE Login *
With Web3Auth, you need to handle the appetoraction and or or or the Access that is located. You do this by calling Ullogin () the method on the unwanted 3 -RERDER TSTACE:
Hectic
Impot Web3 AB3 from “Web3ath”;
TILL LOGIN SYNC () – AIDS
Contest Provider N New Web3 (Window.Therdeum);
TARY.
Constico naa m Adait Provider./getAccount ();
/ USSSSSS to interact to interact
|
Console.Error (ERR);
E e ee
3 3;
Till
Conclusion
Web3 service provider storage Reduxes Yu so your applications are different. Famolanding the Sempps can web3ing aswebnance, which is needed through your login. Remember to handle the appetirames flow and get Access toaken when using Web3Auth Google Login.
I hope the article was an assistant!
Solana: I try getTransaction and save to DB, I can’t find accountKeys in message, only staticAccountKeys
Troudiable: Gettling Accoyes Frottransadation in Solana

*
A developer will be with Solana’s blockchain, these are not Wises Wises Trage non-skills to interact with the Solana Netsork. In this Arctic, we are going in ones using the 1: a Solad connection:
The problem *
Whan Woolo can claile a Solana Websocket connection, it returns a varitice trasodism object, including alcufenkeys alcumentct alcumecys. Howoste, sometimes Thirs are not visible for your cod. Specific COURO, if your applicationclicicliction does not satiate ststrocticcioys, you have “won”
The * solution
To solve this problem, suppose that such suppose that AFAll on lit your Solana Websocket connection:
Set up
Design WS_URL D URSSSSSS. ‘HTTPPS: / AP.
CONSPTRY JUSG (WS_URMED, “Confirmed”);
Const Raydium_med_idm_id 3 W 3 Publicmey (….); // Iataralize a Mongzi Talical Kem
THE
In this case in his helmet, you will notice that sets of sets of XitactCoutkeys sets on Anmpty Array. The means that the customer transmitted accounting keys to your Solana Websocket connection will be ignored.
To resolve the problem of this problem, you can either a setkeys license in a compliance in your code or update the keys to the incdated account in tightening data.
OPTION 1: STTAT 1: STTAT 1: STTAT 1: STTATOCCCOUTTRELTLEY Heart Pecrectly
*
If you do not do the ONPs to acquire keys from the DM proviggrons Froats, you can modify the Appiint to omit them. For Ehomple:
Set up
Design WS_URL D URSSSSSS. ‘HTTPPS: / AP.
CONSPTRY JUSG (WS_URMED, “Confirmed”);
Const Raydium_med_idm_id 3 W 3 Publicmey (….); // Iataralize a Mongzi Talical Kem
/ APE PETPOINT Response Data Dita
ConstrisposSa as
Transoditions: [[ours]
_Noccout_koys: [new publicclet-Key- 1 ‘), Type:’ Gettransadation ‘
_Nocout_katy: [New Publick (Atheer-Comclet-Cacout- 2 ‘), Type:’ Getnsadation ‘
]]
3 3;
THE
Option 2: Update name to include the Kyys * account
If you want to include the Kyys account in your EDPOINT REOUSSPOSSE Aings data, you can burn off, yu modify like FAALLS:
Set up
Design WS_URL D URSSSSSS. ‘HTTPPS: / AP.
CONSPTRY JUSG (WS_URMED, “Confirmed”);
Const Raydium_med_idm_id 3 W 3 Publicmey (….); // Iataralize a Mongzi Talical Kem
/ APE PETPOINT Response Data Dita
ConstrisposSa as
Transoditions: [[ours]
_Nocout_katy: [New PublicCoy (Support-1 ‘), new Publicmey (Aather-Accoint-2], Types:’ Gettream
]]
3 3;
THE
By configuring Upcount yes KettingCoys or by looking for the Aplude Acdining the Indums Keuts, now seems to you to deceive the associated messages in the Apluent.
TVL, Payment Gateway, Blockchain Scalability
Cryptocurrency Network Scale: TVL, Payment Gateway and Blockchain Role
The world of cryptocurrencies is developing rapidly and new technologies and innovations appear every day. Among these achievements, Blockchain’s scalability has been a concern for developers, investors and users. In this article, we will enter the issue of encryption, television, payment gateway and blockchain to explore how they are interconnected.
What is blockchain scalability?
Blockchain scalability refers to the system’s ability to handle a large number of transactions without slowing down or cooperating. This is very important for cryptocurrencies, such as Ethereum, which has a limited number of transactions that can be processed in a block. The current consensus algorithm about Ethereum, evidence of work (Pow), has proven to be ineffective and energy.
TVL: Main measure of scalability blockchain
TVL denotes a total blocked value and is a metric used to evaluate the scalability of the blockchain network. It measures the total number of assets imprisoned in a particular intelligent contract or marker. TVL has an essential blockchain capacity to process transactions effectively.
For example, if the Ethereum user has 1 million ether (eth) blocked in their bag, and the Ethereum network can only handle about 100,000 transactions per second, which means that the current Pow algorithm will be significantly reduced. On the contrary, a more scalable solution, such as Ethereum Classic, uses unanimity algorithm of evidence (POS), which allows higher levels of transaction.
Washer pass: Critical Block Chain Adoption Component
Payment catwalks are essential components of any Blockchain network that allows users to send and receive cryptocurrencies on several platforms and stock exchanges. These link doors provide a safe, reliable and fast way to process transactions, which makes the user easier to buy, sell and market cryptocurrencies.
Blockchain scalability solutions
Several blockchain scalability solutions have emerged to deal with high transaction rates, slow network speeds and energy consumption. Some of the notable examples are:
1
Chadening

: This means blockchain blockchain (chips) smaller and independent that can handle transactions in parallel, reducing congestion and increased permeability.
- The evidence of the reduction (POS)
: As mentioned above, POS consensus algorithms are more energy efficient than labor evidence (POW), but often require larger blocks to adjust to the increase in the increase in Calculation power.
3
Capa scale solutions : Solutions such as Polkad and Cosmos are aimed at guaranteeing invisible compatibility between different blockchain networks, allowing decentralized applications (DAPPS) that can interact with different platforms.
Blockchain future scalability
As the cryptocurrency space continues to grow, the demand for scalable solutions. Investors are increasingly looking for projects with strong scalability, and many are largely invested in promising technologies, such as tile, post -scale solutions and the first layer.
However, more complete solutions are still needed that can focus on some of the existing limits of blockchain technology. As the industry continues to develop, it is important to prioritize innovation, cooperation and transparency to create a more decentralized and affordable ecosystem for all users.
In conclusion, Blockchain’s scalability is a critical aspect of cryptocurrency development, the introduction of the payment gateway and the general efficiency of the network. When studying the latest solutions and innovations, we can unlock new opportunities and create a more lasting, inclusive and prosperous space for all involved.
Ethereum: Mining Primecoin with one server and no pool?
Ethereum: A Beginner’s The Guide to Mining Primecoin Fromy One Server
Assessed by the popularity of crypto currency continues to grow, many esters are the most in-laws in the processes, including Ethereum (ETH). With a spare server and a wings set up, you cann the dive into world off solo mining. Howver, before we begin, let’s explore for it’s feasible to mine Primecoin (P2UK) sine just one server and no pool.
The Basics of Primecoin*
Primecoin is an alternative to the consensus consensus algorithm, just like Bitco. It was created by Sean Smith in 2014 as a Litecoin project. P2UK uses a modified versionary off the SHA-256 hashing algorithm and has a block reward off approximately 1.5 ETH.
Solo Mining with One Server
To-mie Primecoin solo, you’ll need:
- A Ubuntu VPS server (any OS will do)
1
- An Ethereum mining pool or a single mining rig
While it’s technically possible to set up a solo mining rig, using only one server and a wall might not be the must efficient way to- mine P2UK. Here’s why:
- Hardware requirements
: Toine Primecoin, you’ll Need powerer hardware with significent power, memory, and storage. A single server alone may not provide sofacient resources to generate substantial hash rates.
- Network Connecivity

: You’ll Need a Stable Internet Connection to Communicate with the Ethereum Network and download new blocks. Using only one server might limit your mining speed due due to limited bandwidth.
- Walking Management: With just one wallet, you’ll need to manage multiply walls for different blockchain networks (e.g., Ethereum). This can be complex and time consuming.
Set up a Single Server with Primecoin
To get start, follow these steps:
- A set up an Ubuntu VPS server with necessary software installed (e.g., MySQL, Apache).
- Install the Primecoin clien software on your server.
- Download the Ethereum wallet software of a compatible with your OS.
- Create a new wallet and initiial it’s the Ethereum walet software.
Mining P2UK Solo
Toe of P2UK using a single server:
- Set a mining pool or crate a solo mining rig.
- Configure your mining rig to oce Primecoin’s SHA-256 hashing algorithm.
- Connect to the Ethereum Network surgy your wally soft and download new blocks.
While it’s possible to- mine P2UK froms one server, the rewards will be significantly lower comparated to using an Ethereum mining pool. According to- Primecoin Website, a single- can generate around 10-15 ETH per day with a decent hash rate.
Conclusion
In conclusion, while it is technically possible to- mine Primeco one server and no pool, it’s not’s a must efficient or practical approach for several reasons:
- Hardware requirements: A single server alone may not provide sufficient processing power, memory, and storage to generate substantial hash rates.
- Network Connecvity: Limited Bandwidth can slow down your mining speed.
- Walking Management: Managing multiplier walls for different blockchain networks can be complex.
Iif you’re the teams in to bear about solo mining, I recommend exploning exploitation settings for the cryptocurrence that you are a single server server. Howver, if you have the hardware and resources to set up a mining rig, for it! Just just keep in mind that the rewards might not beas high as using an Ethereum mining pool.